Computer Viruses to Watch Out for: Cryptolocker and Ransomcrypt
Cryptolocker and Ransomcrypt – New, Serious Threats
While Ransomlock Trojans have plagued the threat landscape over the last few years, we are now seeing cybercriminals increasingly use Ransomcrypt Trojans. The difference between Ransomlock and Ransomcrypt Trojans is that Ransomlock Trojans generally lock computer screens while Ransomcrypt Trojans encrypt (and locks) individual files. Both threats are motivated by monetary gains that cybercriminals make from extorting money from victims.
Recently, a new threat detected by Symantec as Trojan.Ransomcrypt.F (AKA Cryptolocker) has been growing in the wild. Trojan.Ransomcrypt.F encrypts data files, such as images and Microsoft Office documents, and then demands payment through Bitcoin or MoneyPak to decrypt them—all within a countdown time period. This Ransomcrypt Trojan uses strong encryption algorithms which make it almost impossible to decrypt the files without the cryptographic key.
What is particularly scary about this new threat is that it is working. People whose data is being held ransom are paying up and there is a legitimate concern for copycats since this has proven to be a successful scam.
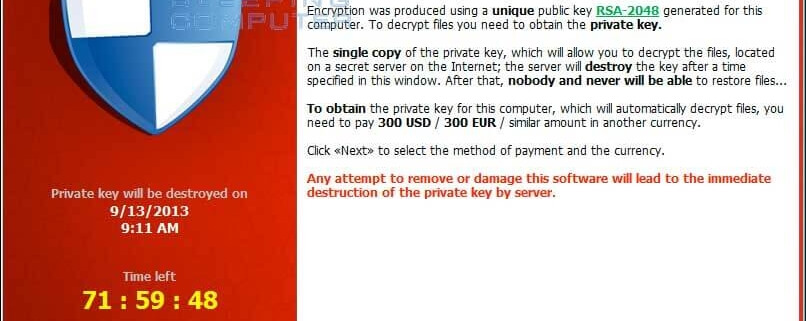
The screenshot below is what pops up if your computer is infected.
How to avoid the cryptolocker and ransomcrypt virus
According to reports from security firms, CryptoLocker is most often spread through booby-trapped email attachments, but the malware also can be deployed by hacked and malicious Web sites by exploiting outdated browser plugins.
Fortunately, there are a couple of simple and free tools that system administrators and regular home users can use to minimize the threat from CryptoLocker malware. A team of coders and administrators from enterprise consulting firm thirdtier.net have released the CryptoLocker Prevention Kit – a comprehensive set of group policies that can be used to block CryptoLocker infections across a domain. The set of instructions that accompanies this free toolkit is comprehensive and well documented, and the group policies appear to be quite effective.
Individual Windows users should check out CryptoPrevent, a tiny utility from John Nicholas Shaw, CEO and developer of Foolish IT, a computer consultancy based in Outer Banks, N.C. Shaw said he created the tool to mimic the actions of the CryptoLocker Prevention Kit, but for home users. So far, he said, the CryptoPrevent installer and its portable version have seen tens of thousands of downloads.
CryptoLocker might be the best advertisement yet for cloud data storage systems.
For further reading on cryptolocker see:
BleepingComputer discussion thread.
Malwarebytes: Cryptolocker Ransomware: What you need to know.
Naked Security (Sophos): Destructive malware Cryptolocker on the loose.
http://www.symantec.com/connect/forums/cryptolocker-and-adc-policies
Reddit thread: Proper care and feeding of your Cryptolocker
Makeuseof.com: Cryptolocker is the nastiest malware ever and here’s what you can do
Ars Technica: You’re infected — if you want to see your data again, pay us $300 in Bitcoins


Leave a Reply
Want to join the discussion?Feel free to contribute!