Website Security: Steps to Protect Your Site From Being Hacked
Recently a client of mine contacted me because his site looked like this:
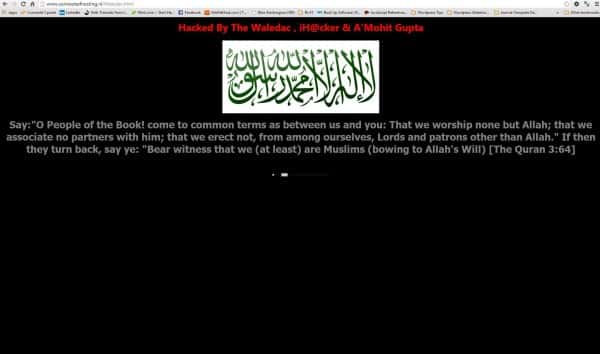
Screenshot of a Hacked Website
78% of malware cases are attributed to outdated core applications, plugins or modules. That means an outdated version of WordPress, an outdated version of a theme, or an outdated version of a plugin.
Seven Steps to Prevent Your Website From Being Hacked
- Backup your site regularly to a location that is different from your website host.
- Update plugins, theme, and WordPress version whenever there is an update. Do not let versions lapse. Updates frequently exist because someone has discovered a security vulnerability.
- Remove themes and plugins that are not in use. Inactive themes and plugins can be used to access your website. Remove anything that is not pertinent to your site.
- Replace plugins that are more than 2 years old and have never been updated.
- Use strong usernames and passwords – a non English word with uppercase, lowercase letters, numbers and special characters.
- Change your nickname so it’s not your username. Otherwise you are giving hackers half the puzzle.
- Use a malware/security service like Sucuri or Wordfence to protect your site.
What to do if your site is hacked?
- Keep a deep watch – hackers usually don’t hurry to mess with your site. They do everything slowly. If you think your site has been hacked, watch everything very closely.
- Hope that you have that backup in hand.
- Contact your web host – try to contact your web host immediately regarding the unnatural activity. Maybe they can help you or maybe they know something about it.
- Change your FTP/SSH login passwords – immediately change the FTP and SSH login passwords. And this time, choose completely different and stronger passwords.
- Change “admin” username. Do not use “admin” as your username. 99% of attacks take place with this username.
- Change password. The hackers know your password. So – change the passwords of all the admin accounts asap. Change the database password as well.
- Forced Logout. All users (and hackers) stay logged in until the cookies are expired. Because cookies will be valid even after the password is changed, you need to force everyone to logout. Go to – https://api.wordpress.org/secret-key/1.1/salt/ generate a new secrete key. Add the whole code in your wp-config.php file. If similar code already exists there, just replace it. This will invalidate all the set login cookies.
- Update WordPress version. If you’re using an older version of WordPress you really need to update it. This might be how hackers hacked you in the first place.
- If the above things don’t fix the situation, there is only one option and that is to create a fresh WordPress installation.
The real lesson here is relatively simple and goes back to that old Boy Scout mantra –
Be Prepared. Have a recent backup of your site. Know how to restore it or who to call in an emergency. Keep your website, content management system, and plugins up to date. Keep all of your username and login information someplace secure because you will need this for your website host and your domain name in an emergency.